Defining a system
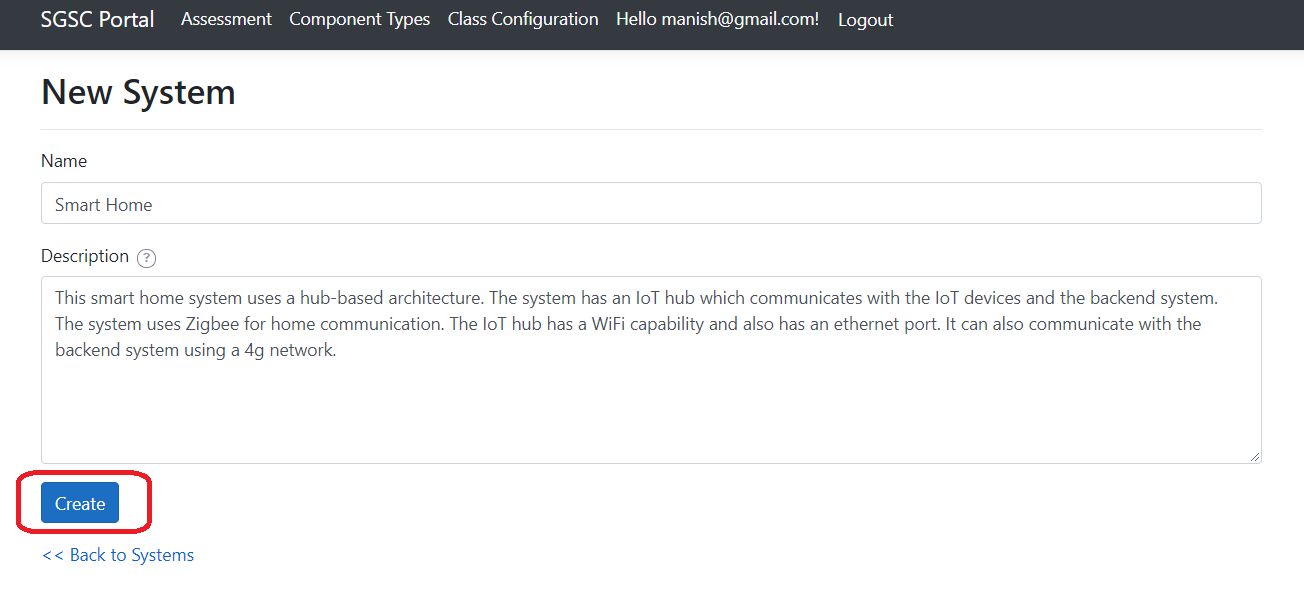
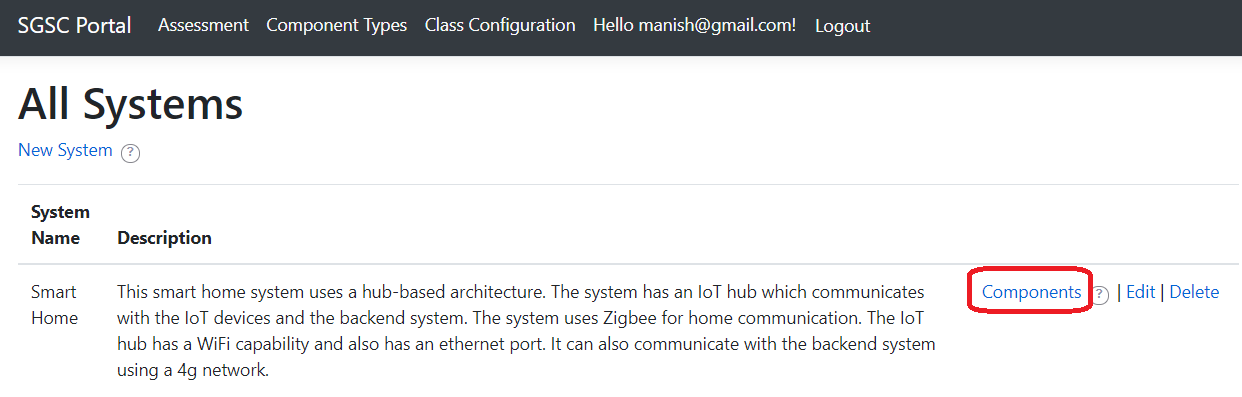
An assessment begins with defining an overall system by giving it a Name and a Description.
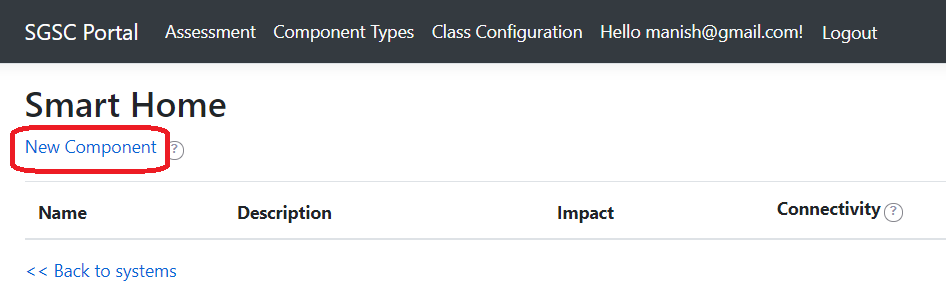
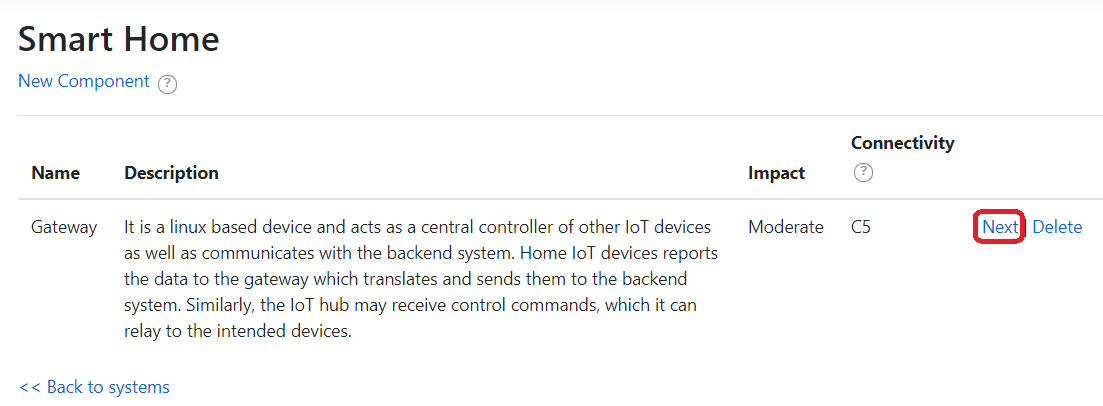
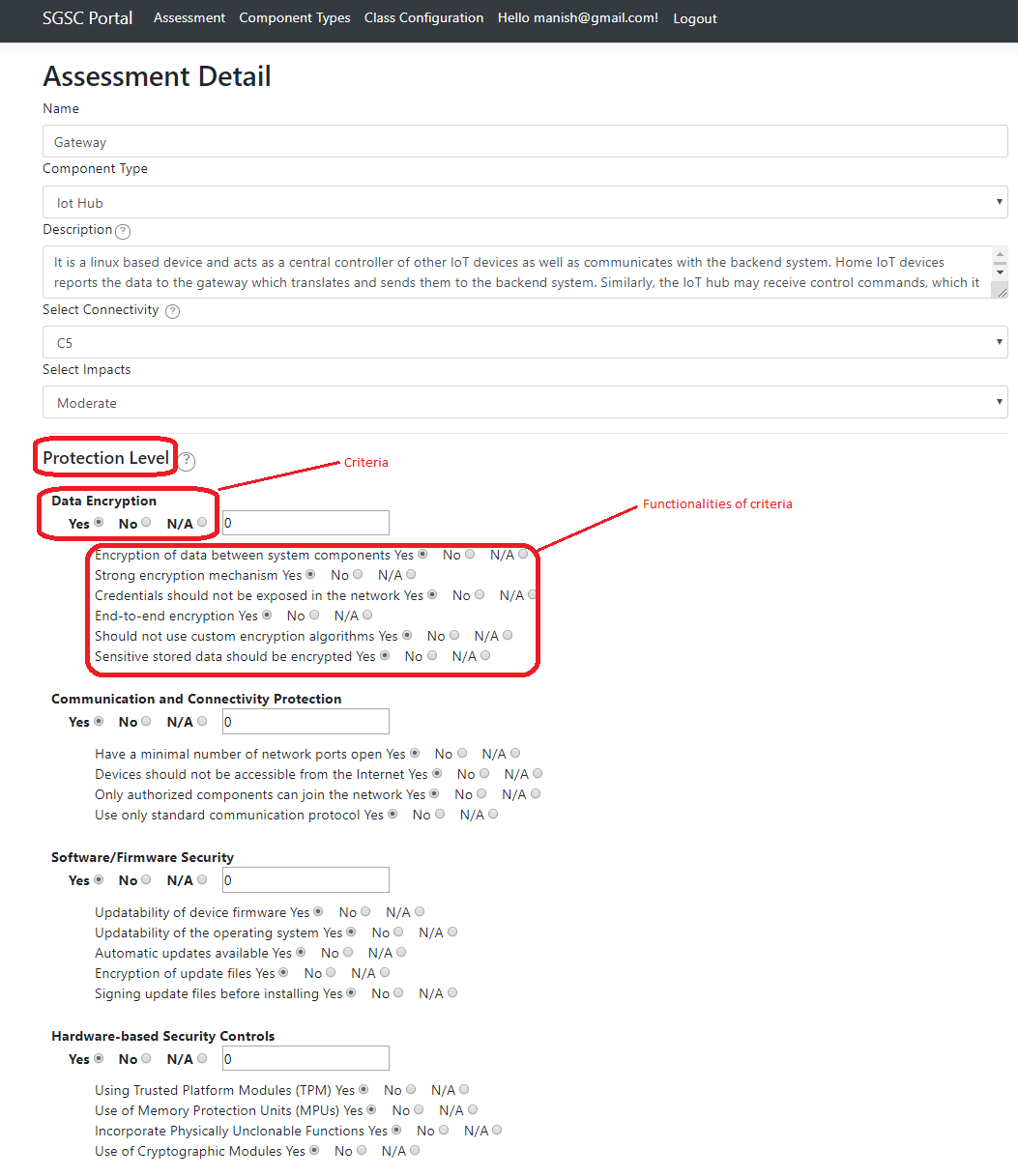
A system is composed of one or more components. Security classification is performed only on a component.
What are components?
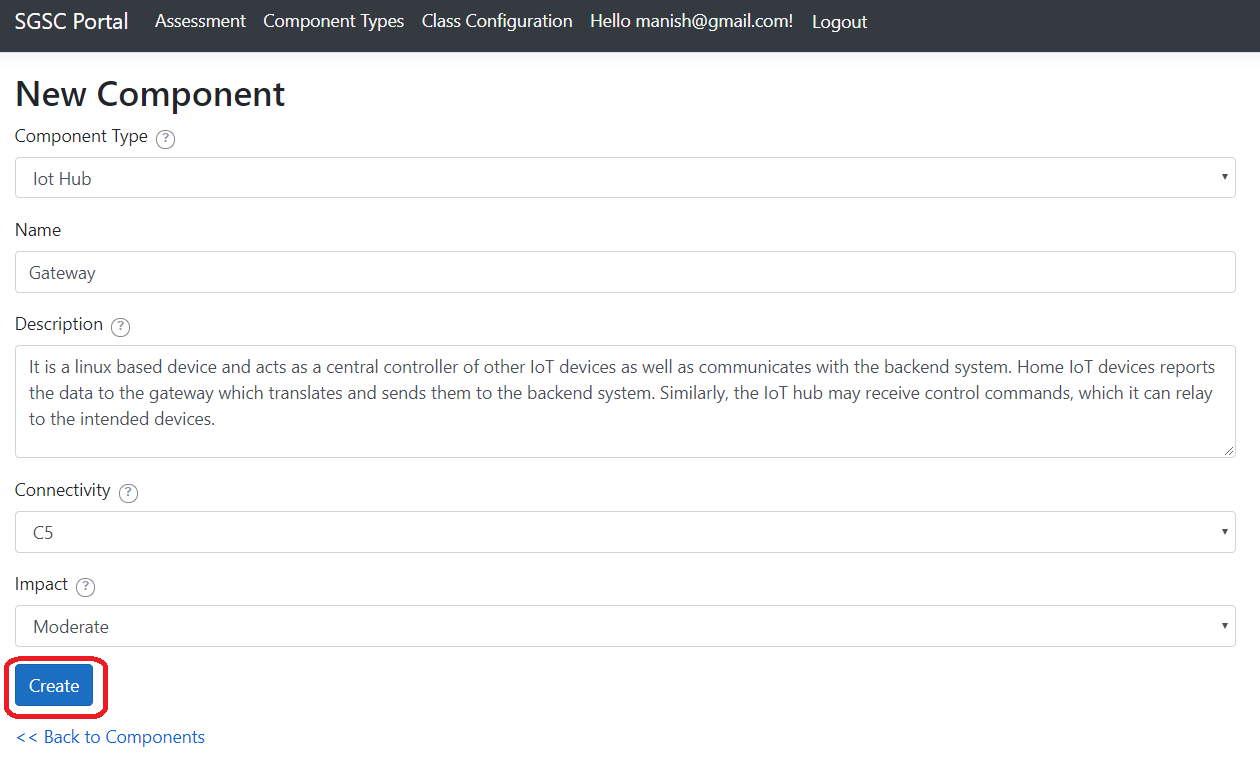
A system is composed of one or more components. To evaluate the security class, each component is evaluated in the next step against relevant criteria
and the corresponding security functionalities. A component belongs to a type. For instance, a component type for IoT systems can be an IoT hub, an IoT device, or a Backend system.
These are default types that any user can use. One can also define specific component types, in the Configuration menu at the top.
Protection Levels
- Protection Level1 (P1): No security mechanisms at all
- Protection Level2 (P2): Basic and/or weak security features
- Protection Level1 (P3): Advanced security features
- Protection Level1 (P4): Advanced security features and basic monitoring
- Protection Level1 (P5): Advanced security features and advanced monitoring
Connectivity
Connectivity represents the surface of a system exposed to attacks. We have considered five levels of connectivity (C):
- C1 Includes completely closed/isolated systems
- C2 Includes the system with wired Local Area Network and does not permit operations from outside the network
- C3 Includes all C2 systems that also use wireless technologies.
- C4 Includes the system with private or leased infrastructure, which may permit remote operations (e.g., VPN, private APN, etc). An example could be allowing to access the corporate network only via VPN. Another example could be the operators being able to connect to their field devices system through their mobile device using a private Access Point Name (APN)
- C5 Includes distributed systems with public infrastructure, i.e., like the C4 category except that the communication infrastructure is public. Example: Web applications and services accessible using Internet.
Exposure
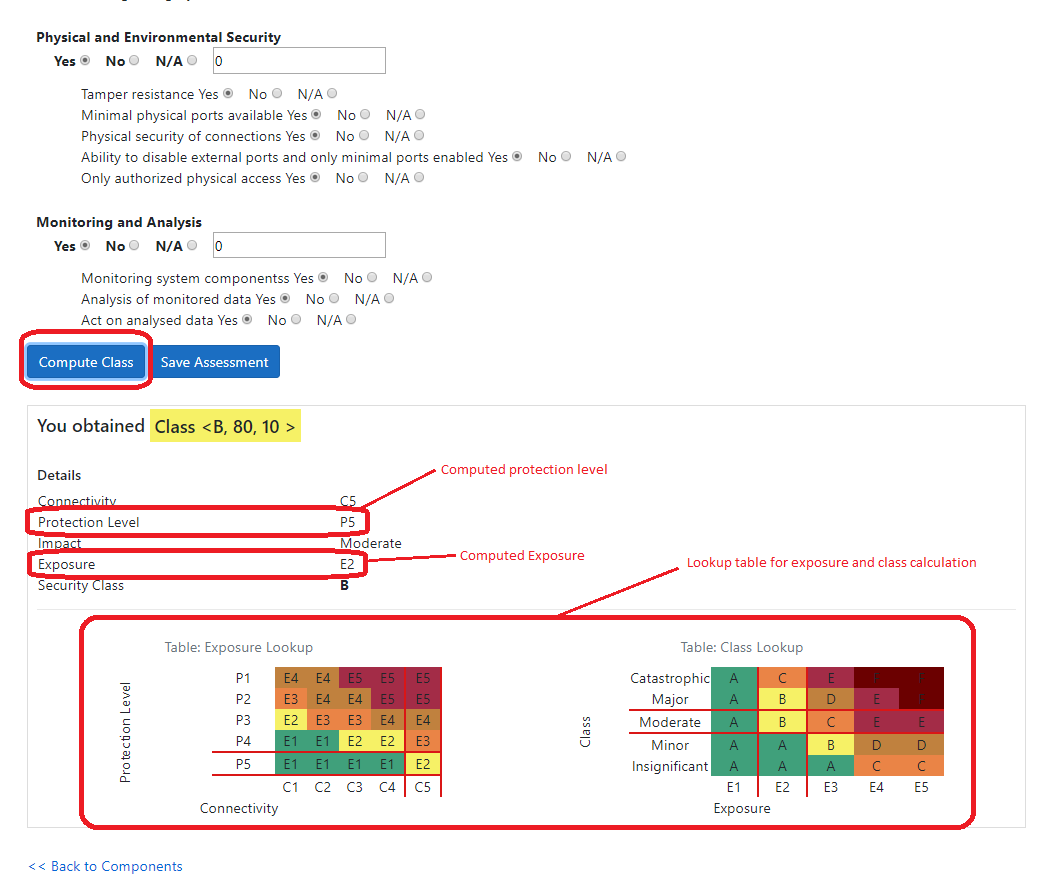
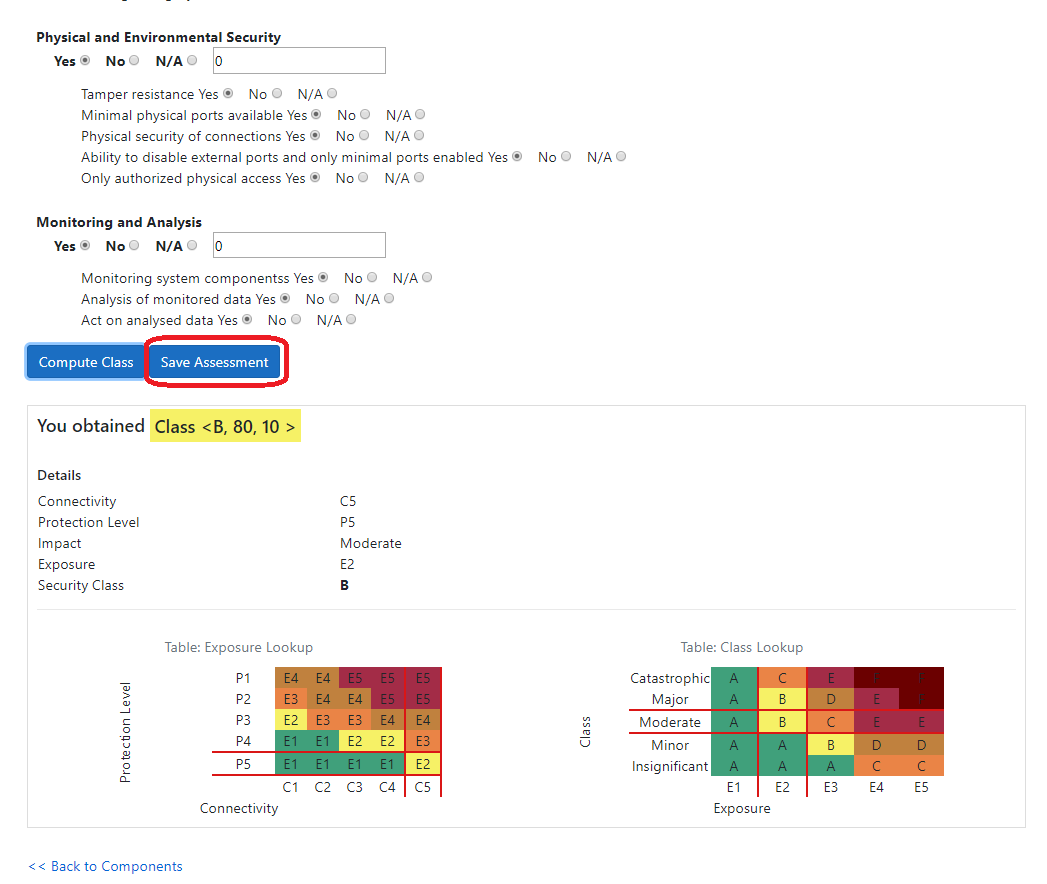
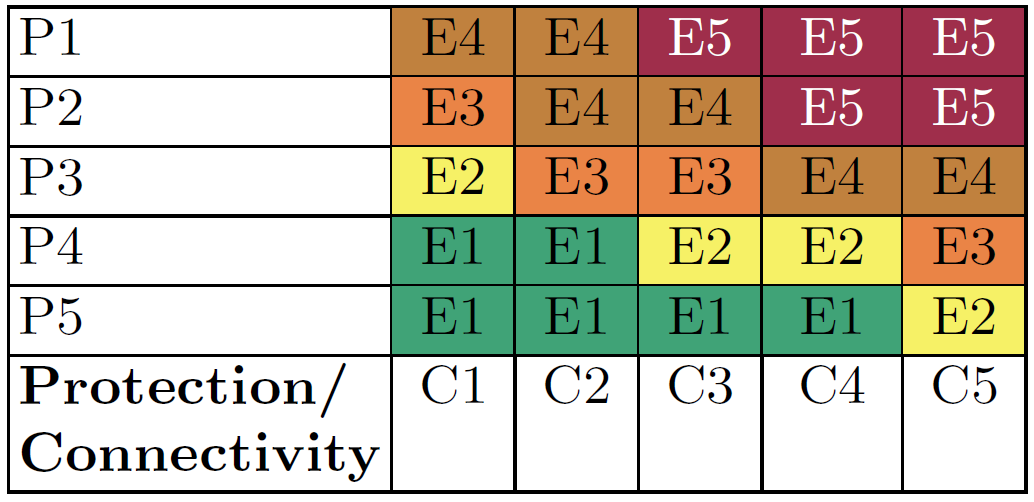
Exposure describes the degree to which a system is available to attacks. Exposure levels range from E1 (least exposed) to E5.
Exposure is defined in the lookup table below, based on Connectivity (e.g., how open the network is) and Protection Level (i.e., how strong the security mechanisms are).
The lookup tables can be changed from the Configuration menu at the top, if they do not quite fit your application domain. But this should be done rarely, and normally one would keep the default ones. One should have/give a good reason for any changes.
Impacts
The impact measures the consequences of an attacker compromising a system.
Similar to impact assessment in risk which involves calculating the impacts on business, government, or society, that could affect
physical infrastructures, human life, environment, economy, etc. It is recommended to select the worst impact of cyberattack.
The Impact is divided into five levels:
- Insignificant
- Minor
- Moderate
- Major
- Catastrophic
| Impact | Financial Impact | Human Impact | Business Reputation | Impacts from Interruption of service |
|---|---|---|---|---|
| Insignificant | <100k € | Accident reported, no sick leave or medical treatment | Negligible Impact | Serious impacts on 1,000 people |
| Minor | 100-500k € | Accident reported, with sick leave or medical treatment. | Adverse local media coverage | Serious impacts on 10,000 people. Disruption of the local economy |
| Moderate | 500k-1.5M € | Permanent disability | Adverse capital city media coverage | Serious impacts on 100,000 people. Disruption of the regional economy. Temporary loss of major infrastructure. |
| Major | 1.5-2.5M € | A death | Adverse and extended national media coverage | Serious impacts on 1,000,000 people. Disruption of the national economy. Temporary loss of a critical infrastructure. Permanent loss of a major infrastructure. |
| Catastrophic | >2.5M € | Multiple deaths | Demand for governmental inquiry | Serious impacts on 10,000,000 people. Permanent loss of a critical infrastructure. |
Security Classification Methodology
Security Classification methodology is based on the ANSSI classification method. However, instead of estimating the exposure
based on the complexity of the system and attacker model (as in ANSSI), this method combines the connectivity (which captures the surface of a system exposed
to attacks) with protection (which describes the mechanisms of the system used to protect the connectivity surface). To compute an overall security class, we look into the
individual components of the system and then aggregate the results upwards. Notably, the Security Classification method does not focus on attackers, as classical risk-based methods do,
but is concerned instead with how a system can be securely built from a design point of view. The benefit is that this method helps system designers to choose the
most appropriate security functionalities to meet the envisaged security class. In addition, the focus on secure-by-design systems is better suited for long term
applicability, as threats and vulnerabilities only represent a snapshot, whereas security classes present an inherent view of an IoT system.
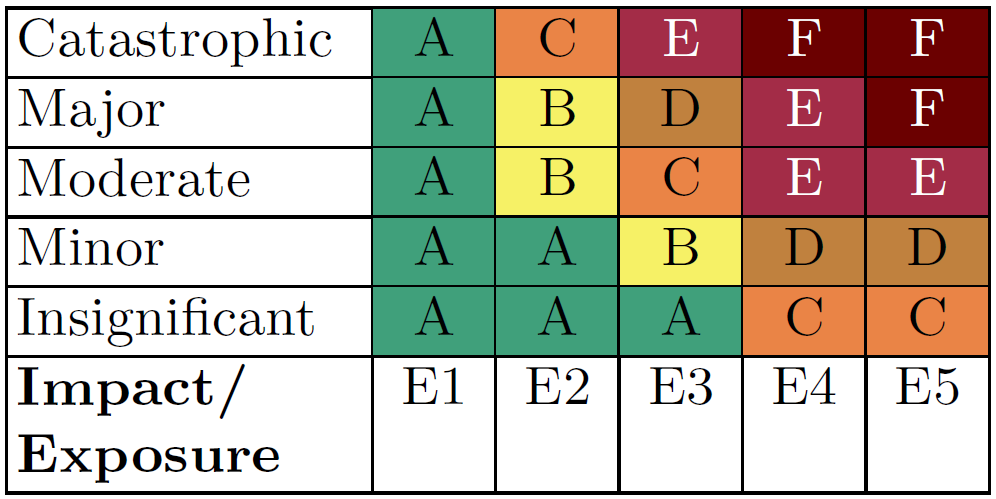
The security classification methodology analyses two aspects: how important a given (sub)system is, and what functionality surface it provides to be attacked,
which we call exposure of the system. Thus, a security class is the result of combining the consequence of an attack on the given (sub)system and the exposure of the (sub)system to the attacker.
It can be improved by reducing either impacts or the exposure of the (sub)system. Class levels vary from A to F where A represents lower exposure (better security functionalilties) and/or lower impacts.
The security classIt can be improved by reducing either impacts or the exposure of the (sub)system.
Class levels vary from A to F where A represents lower exposure (better security functionalilties) and/or lower impacts.